Signature-less Approach for Endpoint Intelligence Platform
Traditional security solutions for endpoint protection use signature-based approaches (e.g. think Anti-Virus solutions) that are generally insecure and ineffective against advanced security threats and targeted malware. Osprey Security’s Endpoint Intelligence Platform uses its patented machine learning based endpoint protection techniques in combination with the traditional signature-based approaches to provide the highest level of security.
Advanced Vulnerability and Patch Management Capability
The Endpoint Intelligence Platform has the ability to perform automatic scanning for vulnerabilities within an endpoint. Besides, from a security perspective, patches are most often of interest because they are mitigating software flaw vulnerabilities; applying patches to eliminate these vulnerabilities significantly reduces the opportunities for exploitation. Organizations that are unable to patch their vulnerable systems effectively and efficiently are highly susceptible to compromises that are preventable. OS-EIP provides a seamless mechanism to identify, acquire, install, and verify patches for vulnerable endpoint products and systems.
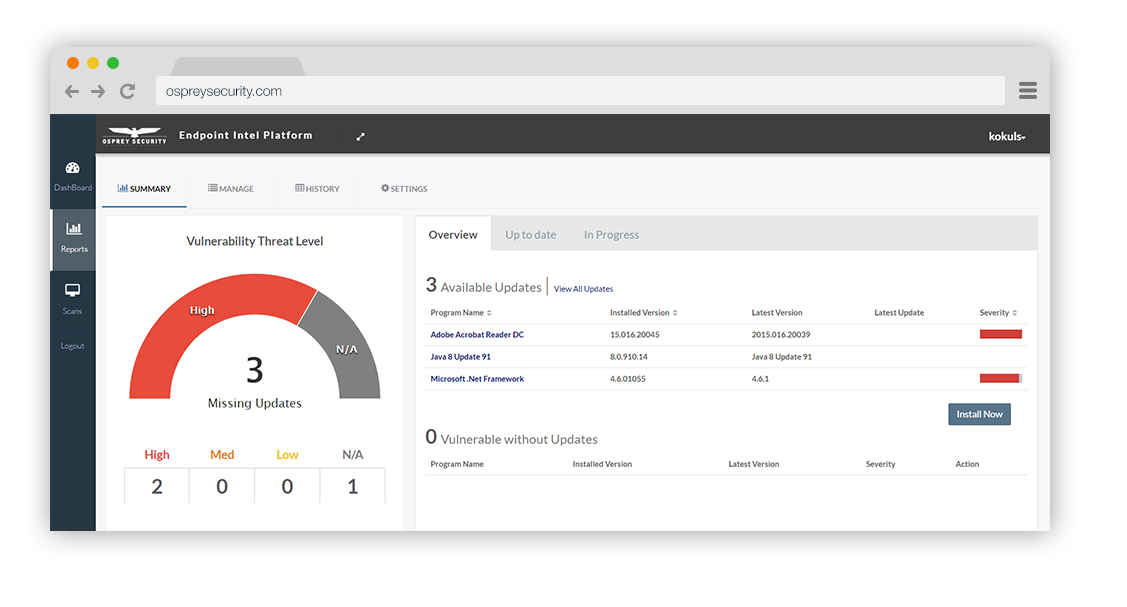
Some key advantages of OS-EIP-Patch Management module are:
Organizations can minimize the time they spend dealing with patching since OS-EIP can automatically scan the system, determine vulnerable systems and software, and if authorized, silently install and patch the system without requiring any user input or large system administration. Organizations can use those resources for addressing other security concerns.
Patch management is required by various security compliance frameworks, mandates, and other policies.
For example, NIST Special Publication (SP) 800-532 requires the SI-2, Flaw Remediation security control, which includes installing security-relevant software and firmware patches, testing patches before installing them, and incorporating patches into the organization’s configuration management processes.
Another example is the Payment Card Industry (PCI) Data Security Standard (DSS), which requires that the latest patches be installed and sets a maximum timeframe for installing the most critical patches.
User and Endpoint Behavioral Analytics
Similar to the next-generation Security Information and Event Management (SIEM) solutions, the Endpoint Intelligence Platform provides advanced security monitoring including user and endpoint behavioral analytics. EIP solution is able to ingest the traditional security intelligence data from various endpoints, networks, and applications within an enterprise and correlates against the data it is generating along with user-centric analytics to provide a much more richer and accurate threat detection capabilities.
Protection against an attacker performing Lateral Movement
Once an attacker has successfully compromised an asset, they try to move laterally within an enterprise, hopping from one system to another, searching for an organization’s crown jewels and other sensitive data. To address this, Osprey Security’s Endpoint Intelligence Platform, through its enhanced visibility and ability to monitor all communication flows from an endpoint and its application of machine learning models and threat intelligence data is able to inspect, and where applicable can quarantine and terminate the connection preventing the compromised host using stolen credentials for example from being able to move laterally from the beach-head asset.
Deception Techniques
The Endpoint Intelligence Platform has the capability to create fake vulnerabilities, generate and plant fake looking sensitive data (e.g. fake credit card numbers using certain BIN ranges), other system shares, cookies, etc. using its patent protection mechanism. As part of its continuous monitoring, when an attacker tries to access these resources or other planted data, our security models can detect and in-turn learn about the attacker’s behavior and patterns.
Cutting-edge Security and Data Visualization
Osprey Security’s Endpoint Intelligence Platform provides some of the most advanced and beautiful data visualization providing an organization’s Cybersecurity Operations Center (SOC) an ability to act of data vs. parsing through data.